Cloud platforms now form the backbone of modern business operations. They support collaboration, data storage, analytics, and increasingly, artificial intelligence workloads. Cloud accounts often contain years of personal and commercial information. They may store financial records, identity documents, business communications, and authentication credentials.
This reliance has delivered efficiency and scale, but it has also introduced a distinct set of cybersecurity risks.
Why cloud environments amplify cyber risk
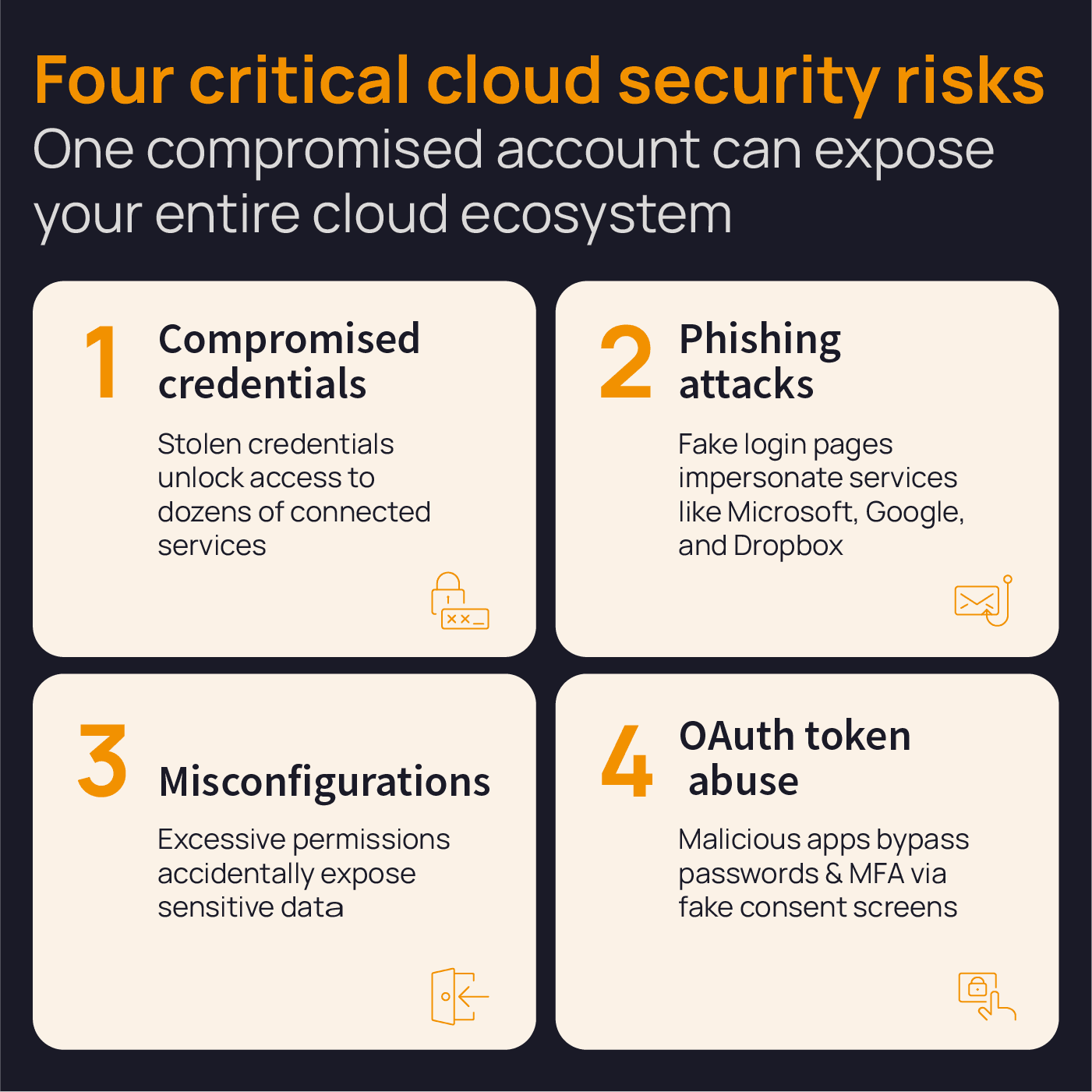
Unlike traditional infrastructures, cloud environments are highly interconnected. This means that one compromised user account can expose multiple applications, data repositories, and partner systems. Attackers understand this concentration of value and are focusing greater effort on cloud‑based targets.
One of the most common risks comes from compromised credentials. Cloud platforms often act as central identity providers for dozens of services. If an attacker steals login credentials, they can move swiftly across connected systems.
Compounding the problem, many firms now rely on a mix of cloud platforms, stitched together with on-premises systems and Software-as-a-Service (SaaS) applications. This makes it challenging to for security teams to maintain oversight and control.
Phishing attacks targeting cloud users
Phishing remains the primary method for gaining that access. Attackers imitate trusted cloud providers and send fake invitations to collaborate on documents or warnings about data storage limits. These messages direct users to fake login pages that harvest their login credentials.
Cloud misconfiguration and excessive permissions
Often, storage buckets, databases, or virtual machines are deployed with overly generous access permissions, making sensitive data accessible to outsiders.
OAuth‑based attacks and token abuse
In an open authorization (OAuth) attack, the attackers trick a user into installing a malicious app that asks for access to their cloud systems. When the user grants permission, the attackers can access their account, bypassing passwords and multi‑factor authentication.
Building resilience through identity and access management
Defensive strategies must shift from isolated controls focused on single points to broad, systemic resilience.
Least privilege access
Ensures users must receive only the permissions they need for their roles. This prevents attackers from moving laterally through a domain if an account is compromised.
Multi-factor authentication
Deploy multi‑factor authentication (MFA) on all your accounts and systems. Though it’s not impregnable, MFA significantly reduces basic credential theft.
Configuration management and continuous security auditing
Audits your cloud services and storage settings regularly. Automated tools can identify risky settings before attackers find them.
Encryption and secure network design
Encrypt data in transit and at rest. This limits the danger from intercepted network traffic or unauthorized access, helping to prevent man-in-the-middle attacks.
Security awareness training
It’s reported that 68% of data breaches involve a human element (source: Verizon 2024 Data Breach Investigations Report). The threat from social engineering tactics demonstrates how cybersecurity depends on people and their actions as much as on technology.
Human behavior remains one of the most important variables. Provide security awareness training to so that everyone in your organization is aware of the risks from social engineering, and can recognize suspicious requests and messages.
The value of proactive threat intelligence
Although the threat landscape is evolving rapidly, the danger from compromised credentials remains constant. 80% of successful cyber attacks use stolen personal data, while phishing and social engineering remain key attack vectors in a cloud-based world.
CTI solutions such as Cybercheck help by continuously monitoring for exposed credentials and personal data, providing early warning to stop attacks before they breach your defenses. Knowing that your personal data is in criminal hands means you can take proactive steps to prevent an attack. For example, changing passwords, blocking cards, or locking down access.
This wipes out the cybercriminals’ information advantage and helps you stop attacks before they happen.







